Con Watch: 5 Best Practices to Prevent Getting Hacked on Social Media
Steve Weisman is a lawyer, college professor, author, and one of the country’s leading experts in cybersecurity, identity theft, and scams. See Steve’s other Con Watch articles.
The recent hacking of the Twitter accounts of many prominent people including Joe Biden, Bill Gates, Elon Musk, Warren Buffet, Jeff Bezos, and Mike Bloomberg highlighted how vulnerable all of us are when using social media. The hacking of your social media accounts can be leveraged by sophisticated criminals to make you a victim of identity theft or to steal your assets. However, there are simple steps you can take to avoid being hacked. Here are five best practices that we all should follow to protect ourselves.
1. Use Strong Passwords
Having a strong and unique password for each of your social media accounts can go a long way toward protecting your security. Unfortunately, too many people use the same password for all of their accounts. This makes you particularly vulnerable to being hacked because in the event of a data breach at one of your online accounts, the hackers now have the password for all of your accounts, which puts you in great jeopardy. (I’ll have Identity Theft for $500, Alex).
Consider using a password manager, which is an app you can use that will create complex passwords for each of your online accounts. All you have to do is remember the one password to your password manager. Some people are concerned that even a password manager can be hacked. While this has not occurred yet, it is a reasonable concern. A good way to generate your own complex passwords for each of your accounts that are easily remembered is to start with a base password, such as IDon’tLikePasswords. This is a good base password that has capital letters, small letters and a symbol. Now make it even stronger by adding a few symbols such as !!! to make your base password IDon’tLikePasswords!!!. This base password can easily be customized for each of your accounts with a few added letters. So, for instance, your Amazon password could be IDon’t LikePasswords!!!Ama. This is an easy way to create complex, unique and easy to remember passwords for each of your accounts.
2. Provide Fake Answers to Security Questions
A security question is an important element of protecting you from being hacked. Unfortunately, enterprising hackers have managed to change the passwords of their targeted victims by answering common security questions with information found through online searches. Often we are our own worst enemies when we provide too much information on social media that is available for a hacker to learn the name of your dog, for instance, or other information that might provide the answer to your security question. An easy solution to this problem is to provide a nonsensical answers. There is no legal requirement that you answer your security question honestly. Thus, the answer to the security question asking your mother’s maiden name can be “firetruck.” You will remember this because it is so silly and no hacker will be able to guess it.
2. Use Dual Factor Authentication
One of the best things you can do to protect yourself from being hacked is to use dual factor authentication on your accounts. With dual factor authentication , when you login to one of your accounts, an additional form of authentication is required. Most commonly, after you type in your password, a special one-time code is sent to your cell phone. You then must enter that code in order to access your account. Even if someone manages to steal your password, they will not be able to access your account. Actress Jennifer Lawrence’s iCloud account containing nude photos of her was hacked when she unwittingly responded to a socially engineered email that appeared to come from Apple asking her to confirm her password. If she had used dual factor authentication, even if the hacker had her password, he would not have been able to access her account.
3. Beware of SIM Swapping
Some very sophisticated hackers have been able to defeat dual factor authentication by SIM swapping your phone number to the hacker’s phone. A Subscriber Identity Module, more commonly known as a SIM card, is an integrated circuit that stores information used to authenticate subscribers on mobile devices, such as cell phones. SIM cards can and are transferred between different devices, such as when you get a new phone. Hackers call your cell phone provider posing as you, answer a security question, and have your SIM card switched to their phone, enabling them to defeat dual factor authentication, because now the authentication code is going to their phone and not your phone. Fortunately, you can set up a PIN or password in order to access your mobile service provider account to protect yourself from SIM swapping. Particularly prudent people can even require that their SIM card only be changed in person.
4. Use Security Software and Install Security Updates Right Away
Make sure you have installed good security software on all of your devices and install the latest updates on your programs, applications, and computer and mobile device operating systems as soon as they become available. Note that even the most up-to-date security software will always be at least a month behind the latest strains of malware. This is why, even if you have the best security software, you should never click on links in emails or text messages unless you have absolutely confirmed they are legitimate. Clicking on links infected with malware sent through socially engineered phishing emails and text messages is the most common way that malware is installed.
Nothing you can do will absolutely guarantee that you will not have your social media accounts hacked, but following these five best practices will go a long way toward keeping you safe.
Featured image: (AngieYeoh / Shutterstock)
No Sweat Tech: Making Good Passwords and Keeping Them Safe
My husband and I recently celebrated our silver anniversary, which means we have generated an entire box set of things to bicker about. He hates the way I load the dishwasher, I hate the way he leaves the TV on. He sometimes thinks my taste in music is suspect, and I think he makes up lousy passwords.
It’s the old married nerd in me: I love him and I want him to stay safe online. This is one argument he lets me win, and he does use better passwords than the ones he initially dreams up. (Perhaps one day we’ll reach a similar detente over my dishwasher-loading skills.)
How are your passwords? Let’s talk about ways to make better passwords — and keep up with them! (And no, you don’t have to be married to an old nerd.)
What’s the Big Deal?
You might be wondering what the big deal is. You’re not famous, you’re not in government work, you don’t have millions of dollars. Why would anyone want to crack your passwords?
Because no matter how not-famous you are, you’re probably doing more and more things online. Do you bank online? Do you buy and sell online? If your email and social media accounts were hijacked, could they be used to scam your friends and relatives out of money? Could they be used to spread malware or ransomware? (Ransomware is a kind of malware that locks up files and makes them inaccessible until a ransom is paid.)
When you choose and use strong passwords, you’re not only protecting yourself, you’re protecting your friends and relatives. Generating passwords isn’t tough, and keeping them organized isn’t tough either.
Ditch the 12345
Before I show you what good passwords are, let me show you what they aren’t. Here’s a list of the worst passwords of 2018, compiled by SplashData. They’re not all common words. There are strings of numbers (12345), proper names (charlie) and even sets of words (iloveyou). These kinds of passwords are not clever and they’re not safe. They endanger your online security.
Passwords should look more like this: ~pX!da.6nx%D/_+6 . It’s 16 characters long, uses special characters and numbers as well as upper and lowercase letters, and it’s randomly generated. Here are three tools to help you make safer passwords.
Secure Password Generator
You may have come across different rules for passwords at different sites. On one site, you might not be able to use special characters for your passwords. On another, you might have to use at least one number and one capital letter. Or your password might be limited to ten characters. Or you might have to use at least 14! Secure Password Generator takes all that into account with several checkboxes for including/excluding symbols, numbers, etc.
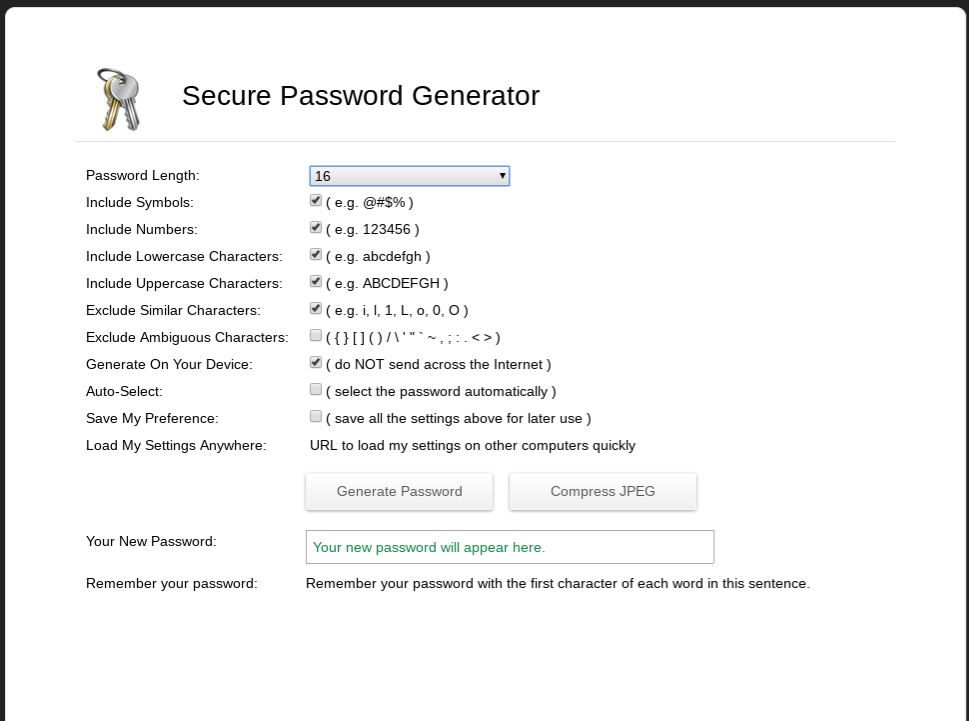
Choose the number of characters you want in your password as well as what kind of characters you want to include. Generally the longer a password is the harder it is to crack; I would argue that it’s better to generate a 12-character password that’s just letters and numbers than it is to generate an eight-character password with numbers, letters and symbols. Eight-character passwords used to be pretty standard, but nowadays they’re too short. Twelve isn’t great; 14 is better, and 16 and up are better still. I have passwords that are over 20 characters long!
One of the things I like about Secure Password Generator is that it gives you a way to help remember the password. Ideally you’ll use a password manager (more about that later) but sometimes you just need a little assistance.
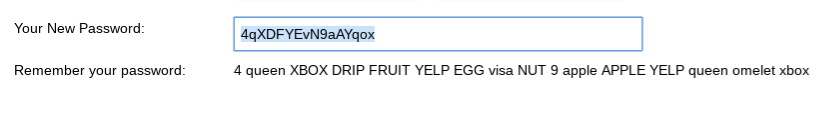
Hugh’s Password Generator
Hugh’s Password Generator works a little differently; you start by providing a sentence and the generator turns it into a strong password.
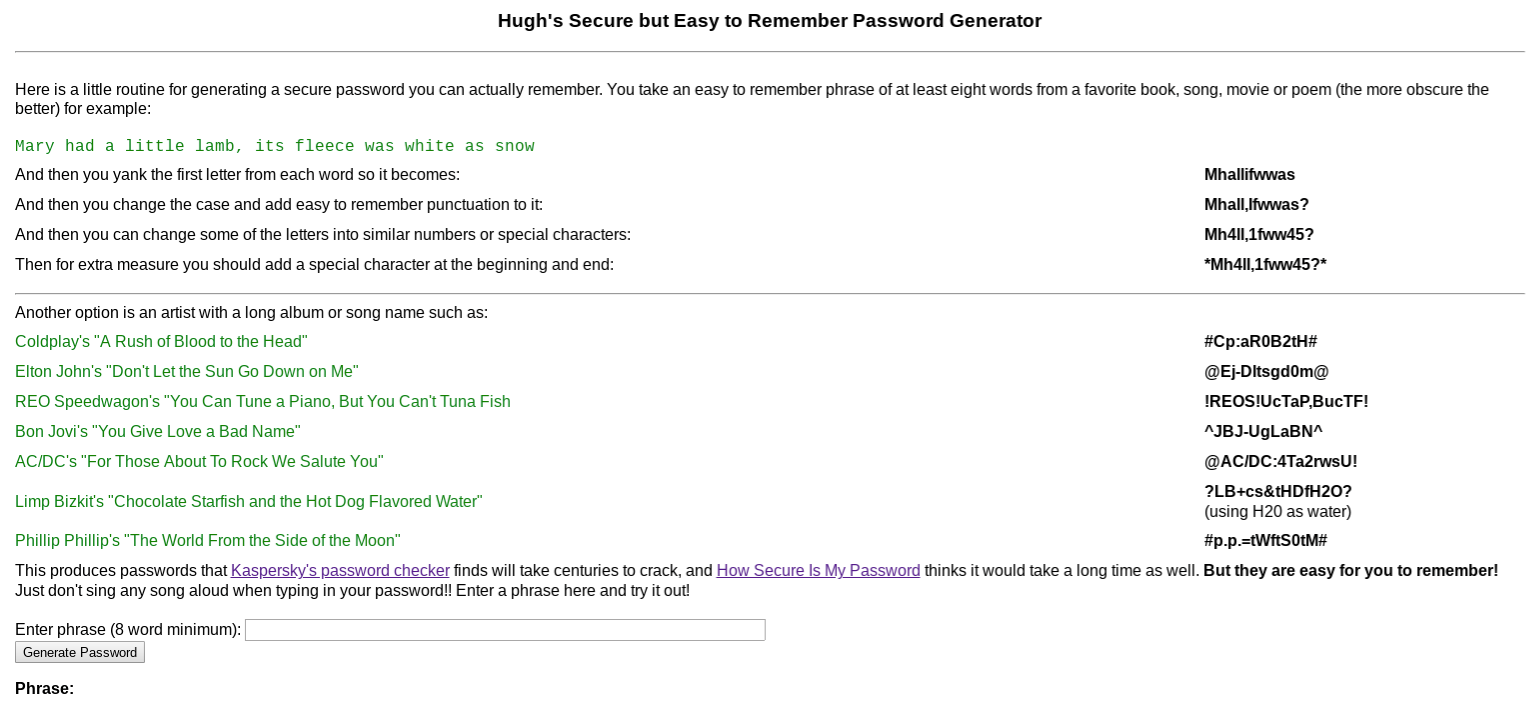
You can use any phrase you like as long as it’s at least eight words. It can be a quote, a song lyric — whatever. I’m going to use the absolutely true phrase “There’s nothing wrong with how I load the dishwasher.”
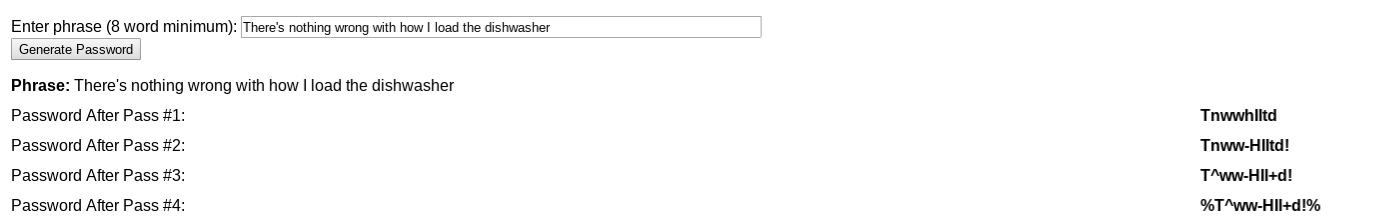
As you can see, Hugh’s Password Generator takes the phrase and runs it through multiple iterations. The first version isn’t very secure (it’s too short and has no special characters), but the last version — %T^ww-HIl+d!% — isn’t bad at all, though I might still add a little to it as it’s only 13 characters long.
Use a Passphrase
The concept of using a passphrase (a series of four or more random words) for a password was popularized by an XKCD comic several years ago. The idea is that four random words is easier to remember and harder to crack than shorter passwords made up of random characters and numbers. There is some controversy about this; passphrases can be significantly less secure if you use common phrases, stick to the most popular words, or don’t use completely random phrases. Use a Passphrase will generate a random phrase for you without those particular pitfalls.
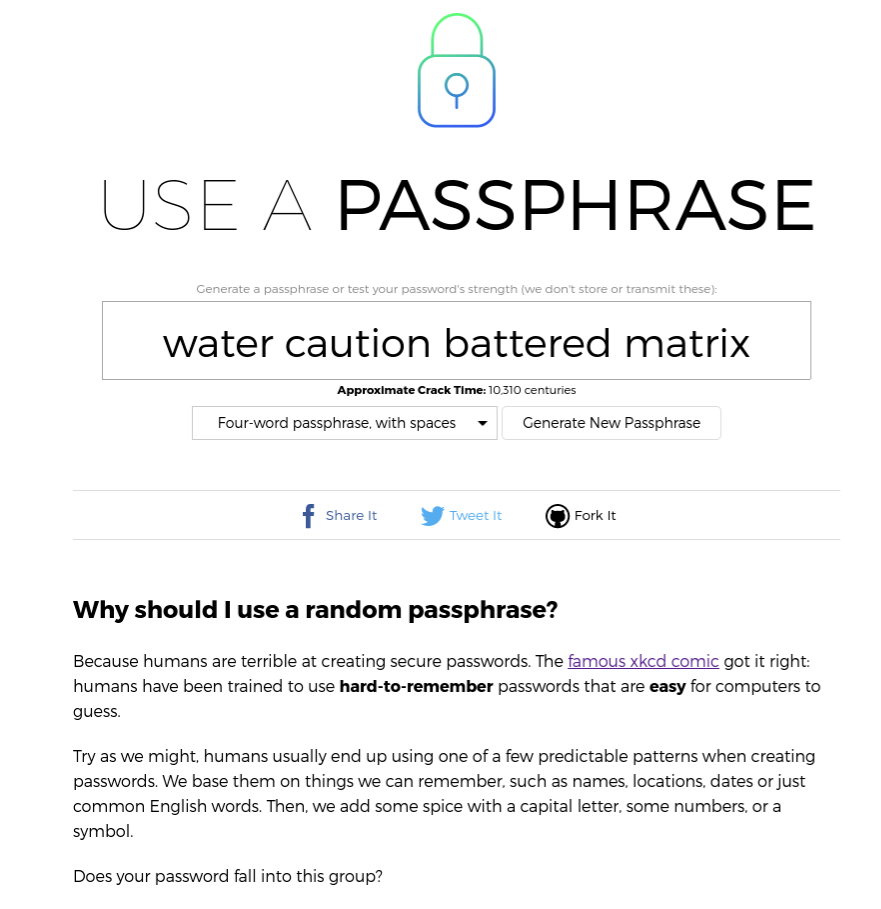
Just open the site and it’ll present you with a random four-word phrase. (You also have the option of making five- or twelve-word phrases.) The site explains why these phrases are secure as compared to randomly generated character strings. Personally, these passwords still make me a bit nervous as I’m afraid they’ll still fall prey to dictionary attacks, but I can understand why you might want to use them if you need a password for something that doesn’t have to be as secure as possible.
At this point you might be wondering how you know which passwords are secure and which aren’t. Some of it is just experience, but there are also tools online that give you an idea of how quickly passwords might be cracked by a determined hacker. How Secure is My Password is one of them. Enter a password and it’ll estimate how long it would take for that password to be cracked, from instantly — a really horrible password like “password” — to ridiculous amounts of time like “113 Septenvigintillion Years” (for a 60-character password). Let’s see how that tool likes the password I mentioned at the beginning of this column, ~pX!da.6nx%D/_+6.
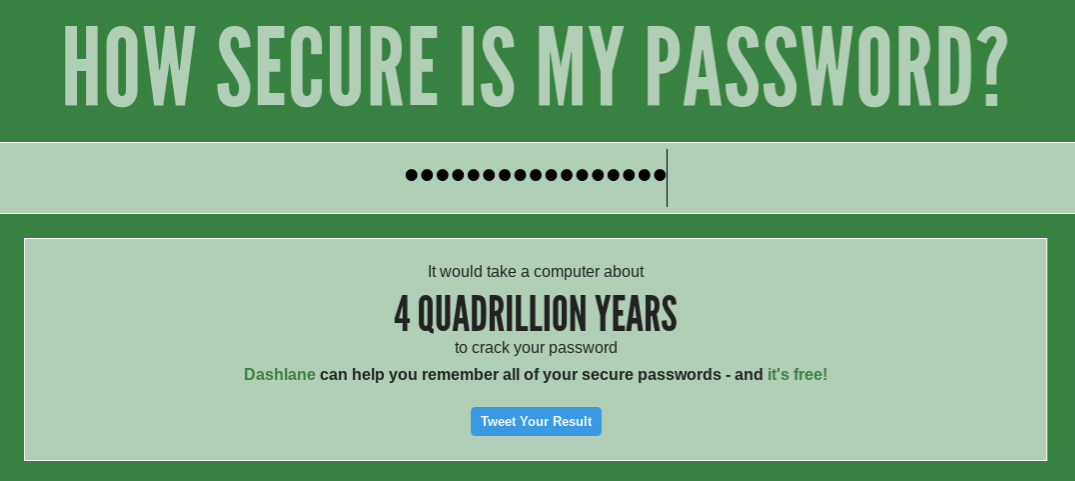
Looks like a good password!
You may also be wondering why you would enter your special private password into a web form? Aren’t you just exposing a password to possible theft and misuse?
That’s a great question. When I am using a password-generating site, I create two using the same rules — one to use, and one to check the quality of the algorithm. For example, I might use Secure Password Generator to generate two passwords — *6rV@S$#?@?kyuGf and Lq\\gm8V6bs]7MnJ — using the same sets of rules about length, what should be included, etc. I will keep the first one private, and paste the second one into How Secure is My Password. That’ll tell me how strong the rules for creating the passwords are without disclosing the password itself.
Password Managers
Now you’ve got a set of much more secure passwords for all the websites you belong to. Now what do you do? Write them on your hand? Put them on a sticky note next to the monitor? Nope; you put them in a password manager, which is a place to park your passwords so they’re easily retrievable when you want to use them. Before I get into the specifics, let me mention a few ways I try to keep things as secure as possible when using a password manager:
- I don’t use the browser extensions. Many password managers have extensions meant to be used in your browser so retrieving passwords is easier. I don’t use these extensions because to me, any time you’re linking your password manager to something else you’re increasing your risk. And sure enough, while I was writing this article I saw that one extension had a security issue. When I need a password, I log in to the password manager’s website for a copy-and-paste.
- I don’t store my email password on my password manager. If I lose a password and need to reset it, how am I likely to do that? By having a reset tool sent to my email. Therefore, to me, my email password is the most important one I have, because my email is a vector to access my other accounts. I store it safely offline; that way, if the unthinkable happens and my password manager is breached, it is still safe.
- I use 2FA. 2FA stands for “two-factor authentication”; that just means that after you enter a password, you have to do something else to verify your identity, like typing in a number you get via text message. I use a YubiKey. My next column will be about 2FA options.
Let’s get into some specifics.
LastPass
LastPass is my favorite password manager, and the one I know best.
As I mentioned I use a two-factor method for LastPass, but I also use a very strong password — it’s 27 characters. Once I’ve logged in, I’m presented with two folders; one with over 100 real passwords and one with a bunch of silly examples I made for this article.
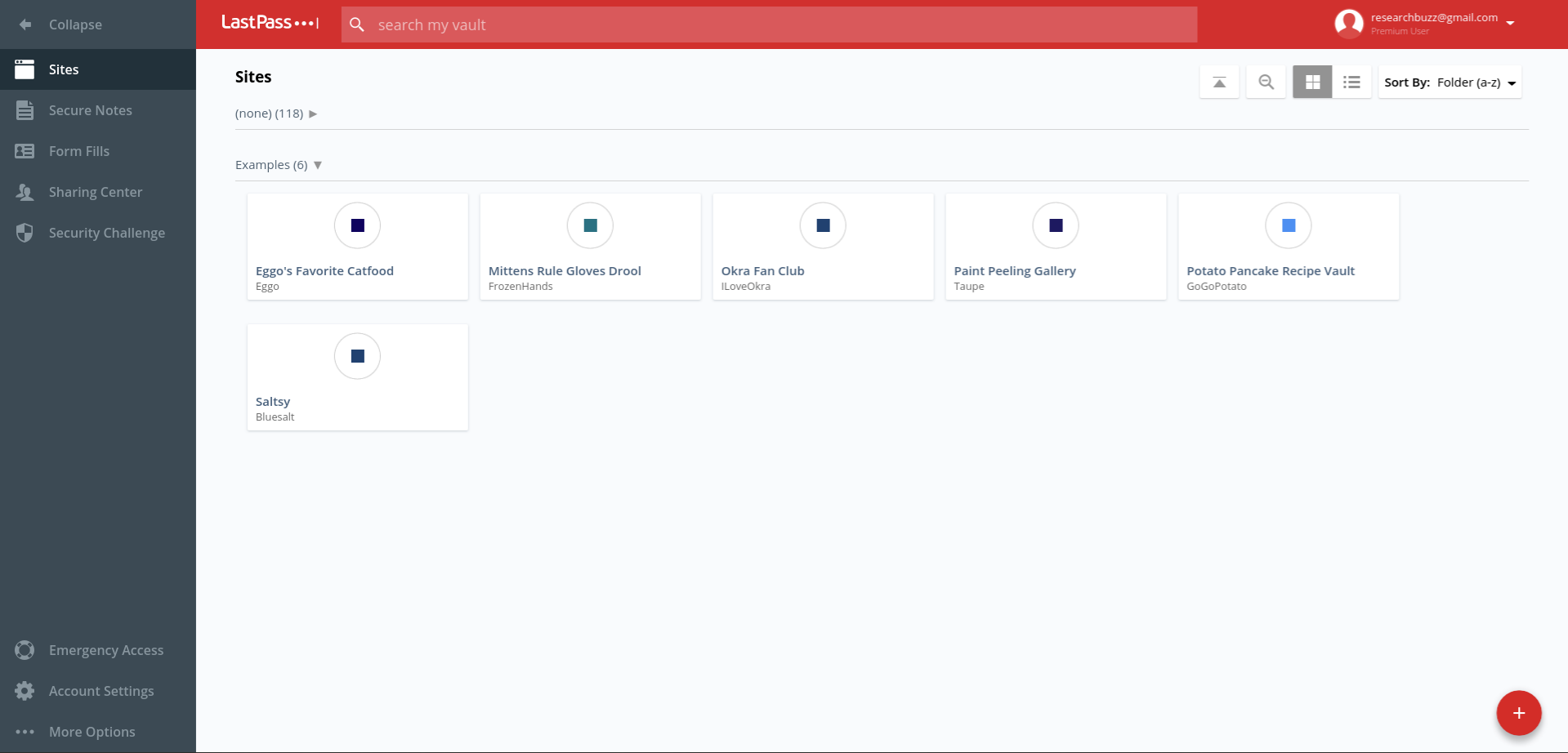
The + in the red circle is used to add passwords; in addition to putting in the regular user name and password combination, you can also add notes and require the master password to be entered again to access that password. (That’s the “Require Password Reprompt” checkbox.)
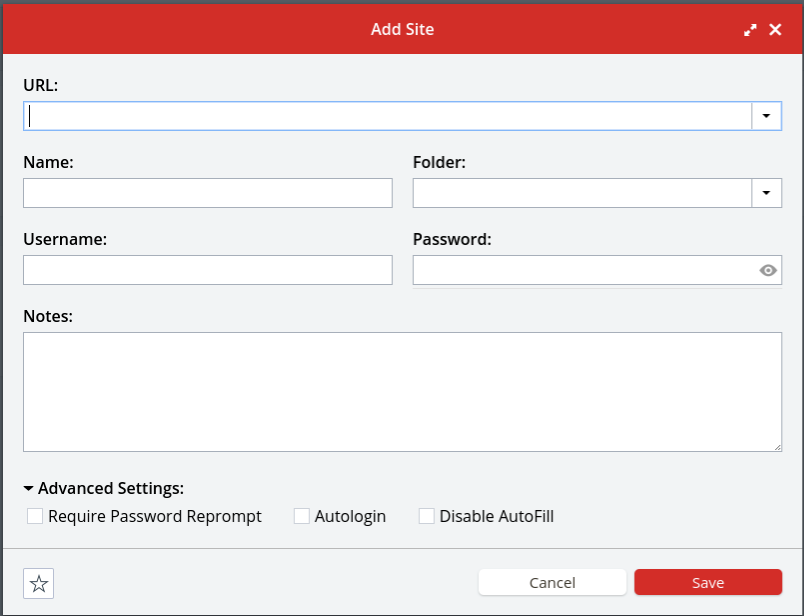
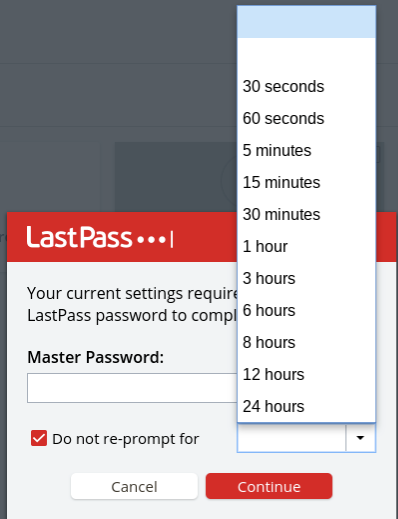
If you try to access one of those passwords, you’ll be prompted both for your master LastPass password and for the amount of time you want that entry’s password to be available without requiring the master password again.
There’s also a place to securely store notes like sensitive numbers, address information, and so on. If you get a premium account (it’s $36 a year) you’ll also get access to 1GB of encrypted file storage as well as the ability to set up emergency access for your account and additional types of 2FA access.
I pay for a premium account; I have a lot of passwords to store and to me it’s worth $3 a month to set up emergency access and use a YubiKey. But honestly, if you’re just one person and you don’t want to the emergency access features, the free account should be fine.
Get busy generating and storing your new, shiny, much-safer passwords, and next time we’ll talk about keeping them even safer via two-factor authentication.
Featured image: Shutterstock
Con Watch: Hidden Dangers in the Internet of Things
Steve Weisman is a lawyer, college professor, author, and one of the country’s leading experts in cybersecurity, identity theft, and scams. See Steve’s other Con Watch articles.
The Internet of Things is the name for the technology by which a wide range of devices are connected and controlled over the Internet. The list of things that make up the Internet of Things includes cars, refrigerators, coffee makers, televisions, microwave ovens, fitness bands, thermostats, smart watches, webcams, copy machines, medical devices, home security systems and even children’s (and adults’) toys.
According to the research firm Gartner, 8.4 billion devices made up the Internet of Things in 2017 and is expected to increase to more than 20 billion devices by 2020.
While these internet-connected devices can be very convenient and helpful, helping you track your calories or unlock your house remotely, they also can have a much darker side.
In 2017 Italian researcher Giovanni Mellini published his findings that he was able to remotely hack into and take control of a sex toy. While a Bluetooth-enabled toy may open up new vistas for consenting adult, it also opens up frightening new opportunities for hackers.
In 2017 the FBI issued a warning to consumers about the privacy and identity theft dangers posed by internet-connected toys for children. These toys are incredibly sophisticated and can tailor their responses to a child’s behaviors and words. The toys often come equipped with sensors, microphones, cameras, data storage components, speech recognition, and GPS. Some of these toys pose a security threat in the way they gather and store information.
For instance, the doll My Friend Cayla has hidden cameras and microphones that can be used to record private conversations over an insecure Bluetooth connection. She has been banned in Germany since 2017, according to the Bundesnetzagentur, the German telecommunications regulatory agency.
The dangers can be quite serious. In 2011 researcher Jay Radcliffe hacked and disabled an insulin pump connected to the Internet, and in 2015 security researchers Charlie Miller and Chis Valasek famously hacked Jeep Cherokees.
The most prominent danger posed by the Internet of Things is when cybercriminals are able to hack your devices and then move within your home’s computer systems to access your routers, laptops, tablets, phones, and computer hard drives. From there, they can steal personal information such as your credit card numbers, bank account passwords, and other information that can be used to make you a victim of identity theft. They can also enlist your devices to distribute malware anonymously.
How to Protect Yourself
- Your first line of defense is your router, so it is important to change the default password that your router came with.
- Next, set up a guest network on your router exclusively for your Internet of Things devices.
- Configure network firewalls to block traffic from unauthorized IP addresses and disable port forwarding.
- Make sure that you install the latest security patches as soon as they become available.
- Use encryption software for the transmission of data and find out where data is stored and what steps are taken to secure the information.
- Limit the amount of information you provide when setting up the accounts for toys. The less information out there, the less is your risk of identity theft.
- Use your router’s whitelisting capabilities, which will prevent your device from connecting to malicious networks.
- Change the default password on each device as soon as you set up the product. Unfortunately, particularly for older devices that are a part of the Internet of Things, security was not built into these devices and they may not even be password enabled.
- Consider using an Internet hub, which is a device that can control multiple Internet of Things devices through a single mobile app that utilizes dual factor authentication and encryption. The manufacturers of these Internet hubs such as Samsung’s SmartThings also provide regular security updates. Not all Internet of Things devices are hub certified, which is why when buying an Internet of Things device you should look for hub certification as an indication that the manufacturer is security conscious.
- Refrain from clicking on links or downloading attachments in emails that may contain the malware that enables a hacker to access your computer and then your entire network of Internet enabled devices. Never click on links or download attachments unless you have absolutely confirmed they are legitimate.
The Internet of Things can be a safe (and fun!) place if you merely take the necessary precautions.