Wit’s End: On Modern Passwords, I’ll Take a Pass
I’ve never gone in for experimental prose. Call me old-fashioned, but I like the basics: structure, coherence, grammar — things like that.
But looking back over my life, I realize I’ve spent countless hours composing edgy, modernist words: random strings of numbers and letters that make a mockery of all meaning. The very sight of them evokes feelings of nihilistic despair.
I’m not trying to be artsy. In fact, I don’t want to make up these words at all. Yet, unless I constantly remember or invent new computer passwords, I am locked out of almost every aspect of my life.
Log into my work laptop? I have to type 52cHeezeball# or no dice.
Pay my kids’ school lunch accounts? 52cHeezeball_@!
Purchase household supplies online? 522CHEezeBALL+++
Check my email? cheezeTOTHEballTOTHEcheezecheezeball_%
Order prints of vacation photos? balmoral*castle(scOTLand)_cheeze?
Watch old sitcoms on streaming video? #princECHARles+cHeeze4ever
Obviously, I can’t remember all these passwords. No one could. When I inevitably forget some random variant of “cheezeball,” I am asked a series of stressful personal questions, a quiz on minor details of my own life:
What was the name of your childhood pet?
Wait, which one? Pass.
Where did you meet your spouse?
Wait, which one? Pass.
What is your father’s mother’s uncle’s middle name?
Um . . . John?
Incorrect! What is your second-favorite food?
Er … tacos, I guess?
Incorrect! Why did William Shakespeare’s last will and testament provide for his wife, Anne Hathaway, to inherit his “second-best bed”? What was Shakespeare implying exactly? Was this some kind of diss to Anne?
Well, scholars disagree —
Incorrect! What is your sun sign in the Zodiac astrological system?
Virgo.
What house is that sign’s ruling planet in right now?
I don’t really keep track of —
You have made too many incorrect guesses. Your account is now locked for suspicious activity. Please contact customer service.
How did we get here? When I was growing up in the 1970s and 1980s, people conducted business in person. If you wanted to buy something, you dragged a squirming child to the store, paid with cash or check, apologized for the mess your child made, and left.
For office work, you rolled a blank page into the electric typewriter and started typing — real sentences with subjects and verbs! Not gibberish.
I first needed a password in college to use the school computer lab. “No problem,” I thought. “I’ll just use ‘cheezeball,’ a simple term I can hold in my fresh young brain.”
But over the decades, passwords horribly multiplied and morphed until we reached the present state, which some have described as a “nightmare.”
That’s a quote from Fernando Corbató, who created the first computer password as a scientist at the Massachusetts Institute of Technology in the early 1960s. In a 2014 interview with the Wall Street Journal, Corbató — by then a trim, cheerful man of 87 — explained that he was trying to keep researchers from “needlessly nosing around in [each other’s] files.”
But in the 2010s, he said, “I don’t think anybody can possibly remember all the passwords that are issued or set up. That leaves people with two choices. Either you maintain a crib sheet, a mild no-no, or you use some sort of program as a password manager.” Corbató himself kept “three typed pages” of passwords and estimated he had used 150 different ones over the years.
In fact, the use of non-computer passwords dates back to ancient times. One of the earliest recorded passwords was “shibboleth,” a word that makes you sound drunk even when you say it correctly.
In the Old Testament Book of Judges, after two tribes engaged in battle, the winning tribe posted guards at the river so their enemies couldn’t escape. Anyone trying to cross the river was forced to say “shibboleth,” which the tribes pronounced in different ways. One fellow came along and said: “Er . . . sibboleth?” Incorrect! He was promptly slain.
From the beginning, it seems, passwords have been mildly absurd. In 2003, they became more so with the publication of password tips by the National Institute of Standards and Technology. As the Wall Street Journal reported in 2017, the agency “advised people to protect their accounts by inventing awkward new words rife with obscure characters, capital letters and numbers — and to change them regularly.”
These rules were widely adopted by government and corporations, yet the NIST staffer who wrote them, Bill Burr, remarked in 2017: “Much of what I did I now regret.” By then retired and with the benefit of 20/20 hindsight, Burr admitted that constantly-changing passwords, larded with nonsense characters, actually don’t work very well.
Great, now you tell me! When I am neck-deep in the Cheezeball Variations and every function I perform is locked away behind a Cheezeball Wall, or CHeezeWaLL_9$8, because that’s just how I think now.
The most unsettling thing about today’s passwords is that they don’t stand between you and enemy territory or exclusive clubs. Unlike a Roman soldier in 300 B.C., I don’t need a watchword to protect my garrison from barbarian hordes. Unlike in the Prohibition Era, I don’t need a code to get into an underground speakeasy where people are singing “shibboleth” with boozy abandon.
Instead, I need complex passwords to pay the water bill and email my mom. The secret space is my own life, and the codes reside in my own faltering memory. What if, one day, I simply can’t remember “cheezeball”? Is “the cloud” going to recognize me somehow and allow me back into my virtual world? Not likely.
Luckily, there will still be a few who know me without passwords. My husband and kids will not require verification of my identity. My loyal dog will not insist on two-factor authentication.
And when I join the ultimate secret club, I doubt I’ll have to recite random numbers and letters. Passing on will be password-free. I expect it will go something like this:
“Hello, it’s me.”
“Oh, hello! Come on in.”
Featured image: Shutterstock
No Sweat Tech: Making Good Passwords and Keeping Them Safe
My husband and I recently celebrated our silver anniversary, which means we have generated an entire box set of things to bicker about. He hates the way I load the dishwasher, I hate the way he leaves the TV on. He sometimes thinks my taste in music is suspect, and I think he makes up lousy passwords.
It’s the old married nerd in me: I love him and I want him to stay safe online. This is one argument he lets me win, and he does use better passwords than the ones he initially dreams up. (Perhaps one day we’ll reach a similar detente over my dishwasher-loading skills.)
How are your passwords? Let’s talk about ways to make better passwords — and keep up with them! (And no, you don’t have to be married to an old nerd.)
What’s the Big Deal?
You might be wondering what the big deal is. You’re not famous, you’re not in government work, you don’t have millions of dollars. Why would anyone want to crack your passwords?
Because no matter how not-famous you are, you’re probably doing more and more things online. Do you bank online? Do you buy and sell online? If your email and social media accounts were hijacked, could they be used to scam your friends and relatives out of money? Could they be used to spread malware or ransomware? (Ransomware is a kind of malware that locks up files and makes them inaccessible until a ransom is paid.)
When you choose and use strong passwords, you’re not only protecting yourself, you’re protecting your friends and relatives. Generating passwords isn’t tough, and keeping them organized isn’t tough either.
Ditch the 12345
Before I show you what good passwords are, let me show you what they aren’t. Here’s a list of the worst passwords of 2018, compiled by SplashData. They’re not all common words. There are strings of numbers (12345), proper names (charlie) and even sets of words (iloveyou). These kinds of passwords are not clever and they’re not safe. They endanger your online security.
Passwords should look more like this: ~pX!da.6nx%D/_+6 . It’s 16 characters long, uses special characters and numbers as well as upper and lowercase letters, and it’s randomly generated. Here are three tools to help you make safer passwords.
Secure Password Generator
You may have come across different rules for passwords at different sites. On one site, you might not be able to use special characters for your passwords. On another, you might have to use at least one number and one capital letter. Or your password might be limited to ten characters. Or you might have to use at least 14! Secure Password Generator takes all that into account with several checkboxes for including/excluding symbols, numbers, etc.
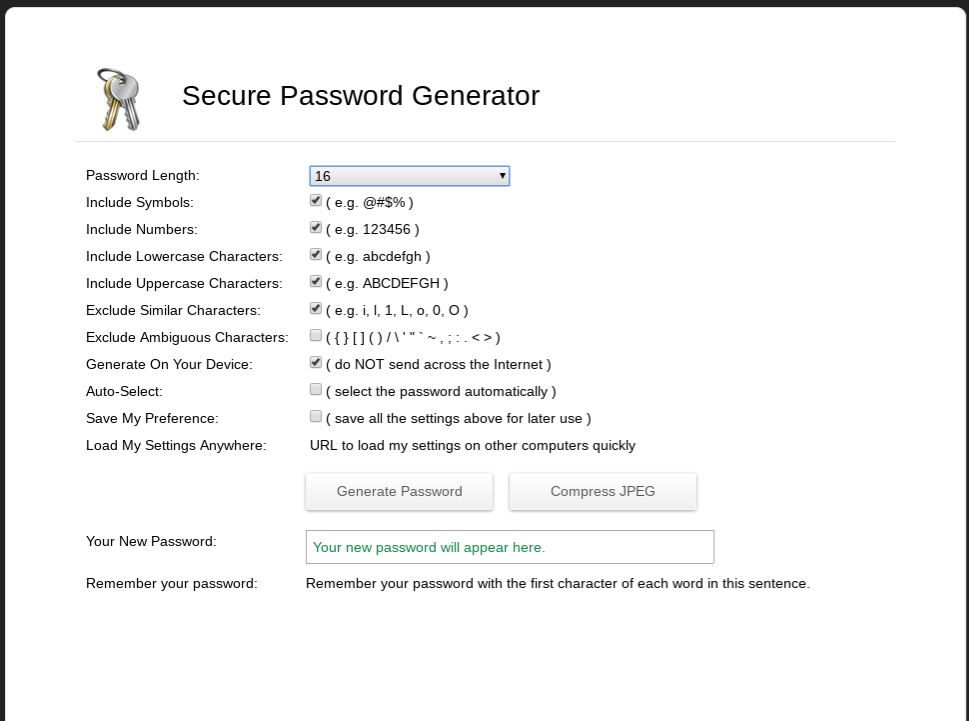
Choose the number of characters you want in your password as well as what kind of characters you want to include. Generally the longer a password is the harder it is to crack; I would argue that it’s better to generate a 12-character password that’s just letters and numbers than it is to generate an eight-character password with numbers, letters and symbols. Eight-character passwords used to be pretty standard, but nowadays they’re too short. Twelve isn’t great; 14 is better, and 16 and up are better still. I have passwords that are over 20 characters long!
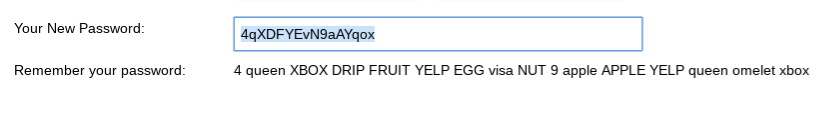
One of the things I like about Secure Password Generator is that it gives you a way to help remember the password. Ideally you’ll use a password manager (more about that later) but sometimes you just need a little assistance.
Hugh’s Password Generator
Hugh’s Password Generator works a little differently; you start by providing a sentence and the generator turns it into a strong password.
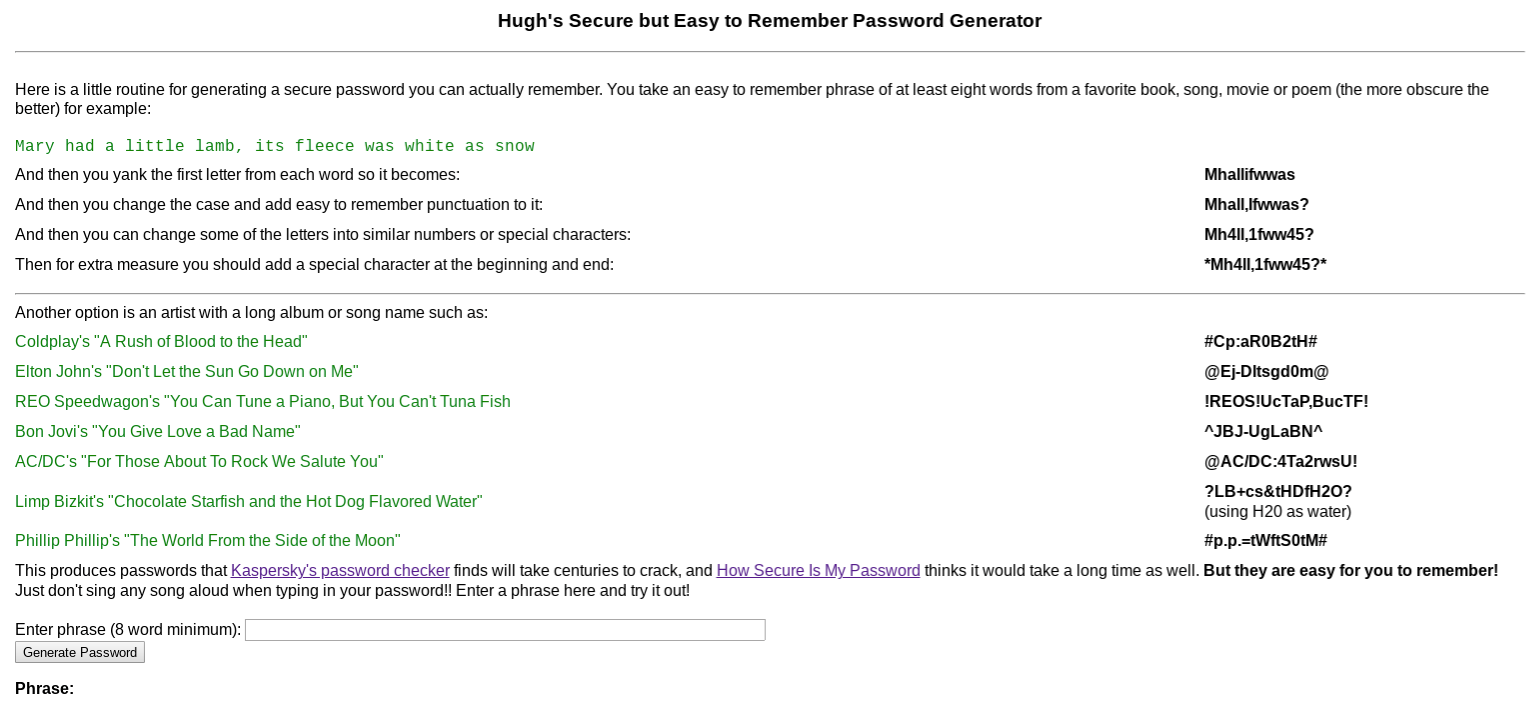
You can use any phrase you like as long as it’s at least eight words. It can be a quote, a song lyric — whatever. I’m going to use the absolutely true phrase “There’s nothing wrong with how I load the dishwasher.”
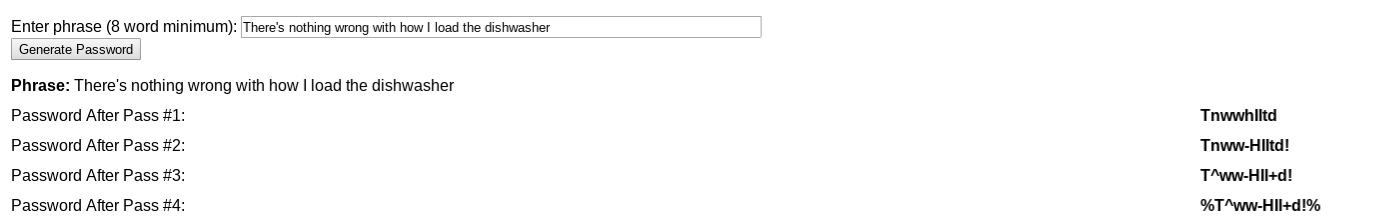
As you can see, Hugh’s Password Generator takes the phrase and runs it through multiple iterations. The first version isn’t very secure (it’s too short and has no special characters), but the last version — %T^ww-HIl+d!% — isn’t bad at all, though I might still add a little to it as it’s only 13 characters long.
Use a Passphrase
The concept of using a passphrase (a series of four or more random words) for a password was popularized by an XKCD comic several years ago. The idea is that four random words is easier to remember and harder to crack than shorter passwords made up of random characters and numbers. There is some controversy about this; passphrases can be significantly less secure if you use common phrases, stick to the most popular words, or don’t use completely random phrases. Use a Passphrase will generate a random phrase for you without those particular pitfalls.
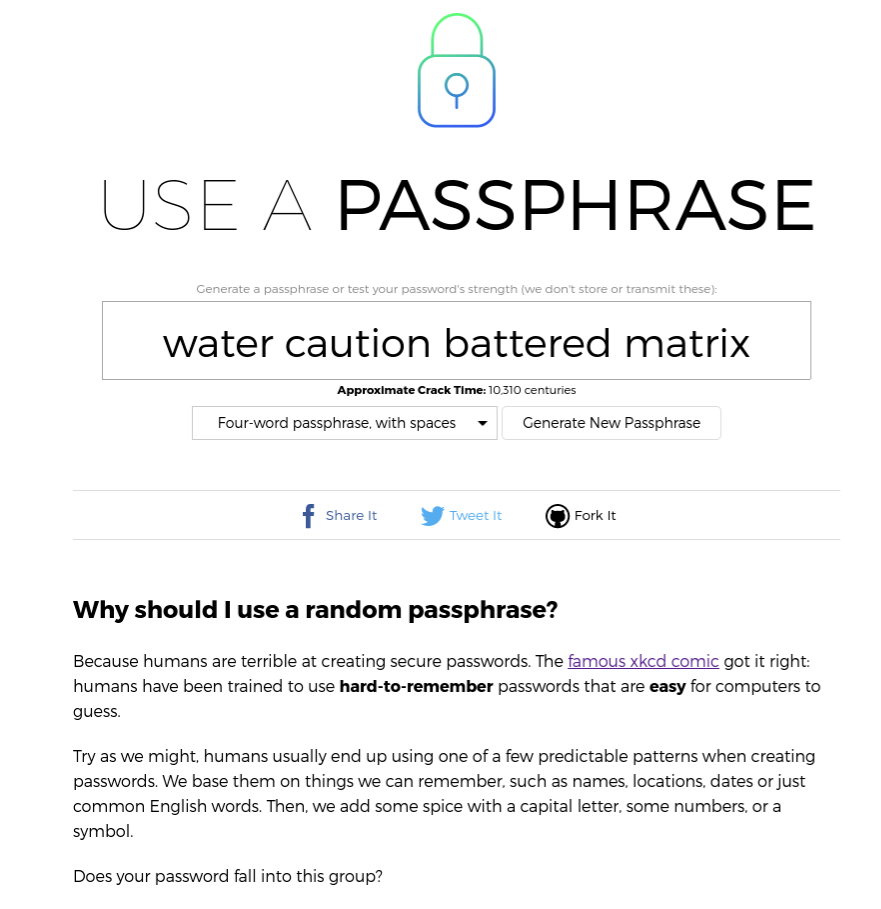
Just open the site and it’ll present you with a random four-word phrase. (You also have the option of making five- or twelve-word phrases.) The site explains why these phrases are secure as compared to randomly generated character strings. Personally, these passwords still make me a bit nervous as I’m afraid they’ll still fall prey to dictionary attacks, but I can understand why you might want to use them if you need a password for something that doesn’t have to be as secure as possible.
At this point you might be wondering how you know which passwords are secure and which aren’t. Some of it is just experience, but there are also tools online that give you an idea of how quickly passwords might be cracked by a determined hacker. How Secure is My Password is one of them. Enter a password and it’ll estimate how long it would take for that password to be cracked, from instantly — a really horrible password like “password” — to ridiculous amounts of time like “113 Septenvigintillion Years” (for a 60-character password). Let’s see how that tool likes the password I mentioned at the beginning of this column, ~pX!da.6nx%D/_+6.
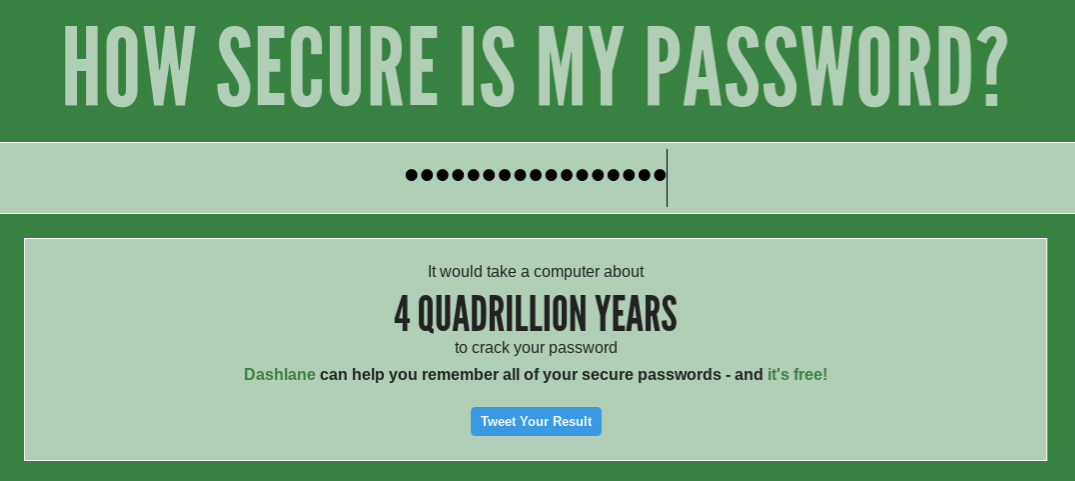
Looks like a good password!
You may also be wondering why you would enter your special private password into a web form? Aren’t you just exposing a password to possible theft and misuse?
That’s a great question. When I am using a password-generating site, I create two using the same rules — one to use, and one to check the quality of the algorithm. For example, I might use Secure Password Generator to generate two passwords — *6rV@S$#?@?kyuGf and Lq\\gm8V6bs]7MnJ — using the same sets of rules about length, what should be included, etc. I will keep the first one private, and paste the second one into How Secure is My Password. That’ll tell me how strong the rules for creating the passwords are without disclosing the password itself.
Password Managers
Now you’ve got a set of much more secure passwords for all the websites you belong to. Now what do you do? Write them on your hand? Put them on a sticky note next to the monitor? Nope; you put them in a password manager, which is a place to park your passwords so they’re easily retrievable when you want to use them. Before I get into the specifics, let me mention a few ways I try to keep things as secure as possible when using a password manager:
- I don’t use the browser extensions. Many password managers have extensions meant to be used in your browser so retrieving passwords is easier. I don’t use these extensions because to me, any time you’re linking your password manager to something else you’re increasing your risk. And sure enough, while I was writing this article I saw that one extension had a security issue. When I need a password, I log in to the password manager’s website for a copy-and-paste.
- I don’t store my email password on my password manager. If I lose a password and need to reset it, how am I likely to do that? By having a reset tool sent to my email. Therefore, to me, my email password is the most important one I have, because my email is a vector to access my other accounts. I store it safely offline; that way, if the unthinkable happens and my password manager is breached, it is still safe.
- I use 2FA. 2FA stands for “two-factor authentication”; that just means that after you enter a password, you have to do something else to verify your identity, like typing in a number you get via text message. I use a YubiKey. My next column will be about 2FA options.
Let’s get into some specifics.
LastPass
LastPass is my favorite password manager, and the one I know best.
As I mentioned I use a two-factor method for LastPass, but I also use a very strong password — it’s 27 characters. Once I’ve logged in, I’m presented with two folders; one with over 100 real passwords and one with a bunch of silly examples I made for this article.
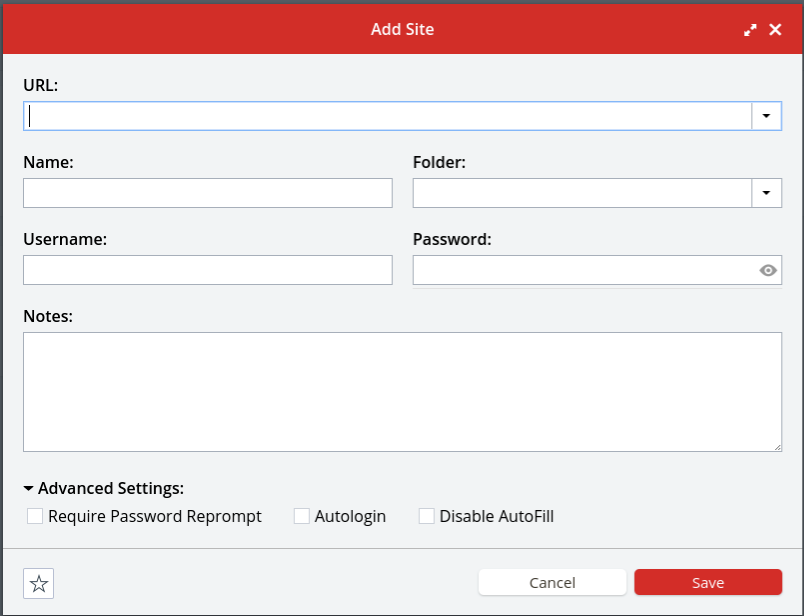
The + in the red circle is used to add passwords; in addition to putting in the regular user name and password combination, you can also add notes and require the master password to be entered again to access that password. (That’s the “Require Password Reprompt” checkbox.)
If you try to access one of those passwords, you’ll be prompted both for your master LastPass password and for the amount of time you want that entry’s password to be available without requiring the master password again.
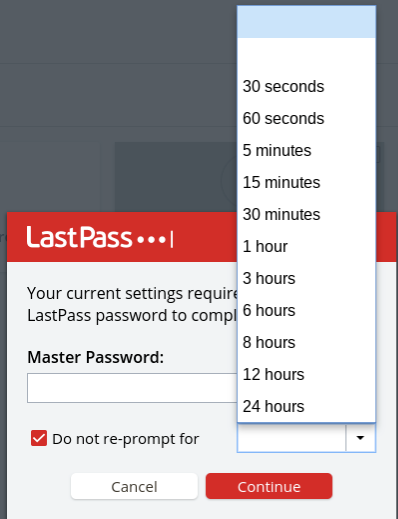
There’s also a place to securely store notes like sensitive numbers, address information, and so on. If you get a premium account (it’s $36 a year) you’ll also get access to 1GB of encrypted file storage as well as the ability to set up emergency access for your account and additional types of 2FA access.
I pay for a premium account; I have a lot of passwords to store and to me it’s worth $3 a month to set up emergency access and use a YubiKey. But honestly, if you’re just one person and you don’t want to the emergency access features, the free account should be fine.
Get busy generating and storing your new, shiny, much-safer passwords, and next time we’ll talk about keeping them even safer via two-factor authentication.
Featured image: Shutterstock