In my last column I talked about passwords and various tools you could use to create strong passwords and make them as secure as possible.
But at the end of the day a password is just a string of characters. And there are ways that someone can get that password that have nothing to do with you. Maybe your bank gets hacked. Maybe a bunch of previously hacked passwords get sold on the dark web. The upshot is someone has your password and access to an account you thought was secure. What else can you do, in addition to choosing a really excellent password, to secure your accounts?
You use a second method of security, one that comes into play after you enter your password. This kind of security is called two-factor authentication (or 2FA). Sometimes it’s also called two-step.
What Is 2FA?
2FA is an additional step you take to confirm it’s you after you enter your password. It might be entering a string of numbers, or receiving a phone call and verifying a code, or even using a hardware token you plug into a USB port.
Why Do You Need 2FA?
You don’t have to use 2FA for every single Internet account you have. Maybe you’ve got a basic GIF tool for making baseball GIFs. If someone got access to that account, it would be annoying, but not that big a deal. Maybe you don’t want to have a second level of security in that case.
But how about your online bank account? Your email? Your WordPress account, if you have a blog? What if someone got into your Facebook account and started pretending to be you and hitting up your friends and family for money?
Unlike passwords, there are different kinds of two-factor to choose from. In this column, I’ll tell you about a method I don’t think you should use at all (though it’s still better than nothing), a method I think is perfectly fine, and my own personal favorite.
Kinds of Two Factor Authentication
A password is simple: you enter it into the password box and you’re logged in. But 2FA is a second step that requires you to confirm your identity, and that can be done in several different ways. There are basically three kinds of 2FA: SMS (text messages), apps, and hardware.
Bear in mind that not all websites support all kinds of 2FA. On some sites you might be limited only to text messages. Another site may require you to use one brand of app over another. Still another site may support only hardware-based 2FA! I recommend you use the strongest 2FA you can, but that might not always be the strongest 2FA out there.
SMS / Text Messages
The first method I’m going to tell you about, and the easiest to use, involves text messages. The bad news is that it’s an inherently insecure method and I don’t think you should use it.
If you’ve got a cell phone, chances are you can send and receive text messages, also known as SMS (Short Message Service).
Because cell phones with text messaging are so ubiquitous, text messages are a popular method of two-factor authentication. For example, you might enter your password on Google. Google then sends a text message to your phone with a one-time code. You enter the code — usually a string of numbers or letters — into Google. Google allows you access to your account, because you have confirmed your identity via your phone.
It’s easy. It’s convenient. And it’s not secure at all, thanks to something called simjacking.
Simjacking is also called simswapping, port out fraud, and sim scamming. The popular term seems to be simjacking, though.
The “sim” in simjacking stands for Subscriber Identification Module. When you sign up for cell phone service, you get a SIM card: a little integrated circuit mounted on stiff material. Unless your provider does it for you, you have to install it (very, very, very, maddeningly carefully) in the phone before you can get service.

This SIM card contains all the information relevant to using your phone. Your name, phone number, authorization to use your provider’s network, security keys, etc. If a crook wants your phone and its information, they don’t need to steal your actual phone. All they need to do is steal your SIM card, or at least the information on it.
That’s what simjacking is all about. A bad guy contacts your cell phone provider and either deceives the support staff or bribes a crooked employee to switch your cell phone’s information from its existing SIM card to a new one controlled by the bad guy. The bad guy now has your phone number. Any calls or text messages directed to the number will be received by the bad guy.
And so much is linked to our phone numbers nowadays! Now that someone has access to your phone number, they might be able to reset the password to your email account. (Many email providers allow you to reset your password with a phone number if you have one associated with the account.) Once they have access to your email, they can easily reset most if not all of your online passwords. And once they’ve reset your passwords and have a fresh set of passwords and your two-factor authentication device…
This isn’t speculative. People have had bank accounts drained, lost cryptocurrency like BitCoin, and have otherwise lost control of their assets because of simjacking.
Maybe you don’t think you’d be a target of such attacks, but leaks of personal information on poorly secured databases and theft of personal information from hack incidents means that thieves may know more about you and your financial situation than you think, and may consider you to be easy pickings. It’s also possible that simjacking might get easier. “The attack does seem to be becoming more widespread with time,” says Keith Dawson, a technology journalist, when I asked him about it. “It’s rather easy to do: it requires no coding or real technical skill. As simjacking gets more publicity, more skiddies will probably try it out.” (“Skiddie” is a shortened form of “script kiddies,” amateur hackers who use others’ scripts and hacks to carry out their dirty work.)
Tom Henderson, principal researcher for ExtremeLabs, Inc., agrees. “Have a trust for mom or a guardian account? Have you checked it recently? I’m not kidding. Latent accounts with high value that can be cashed quickly are susceptible. Yes, bank/trading account security can be good (they check for IP, cookies, browser typification, etc.) but virtually anyone is at risk.”
The upshot of text messages as 2FA is this: they are better in terms of security than just using passwords, but they also have a huge security flaw. You may feel inappropriately secure because you don’t fully appreciate the flaw. I can barely recommend using text messages as a two-factor security method. It’s better than nothing, but it’s still awful.
Happily, there are other methods for two-factor that don’t involve text messages.
A Better Option: Apps
If you’ve got any kind of cell phone, you probably have text messaging. And if you’ve got an Android phone or an iPhone, there’s a good chance you can use apps.
When text messages are used for two-factor, a string of numbers or letters is sent to your phone, and you have to enter that string before you access a site. With apps, you still get a string of numbers or letters, only they exist on your phone. They aren’t transmitted from anywhere and the app is not part of your SIM card. You don’t even have to be connected to the Internet to get them!
Google Authenticator is one of the 2FA apps I’ve used before; it’s available for both Android and iOS. Here’s how it works. Say you wanted to add 2FA security to Facebook. First, install the Google Authenticator app on your phone. Then go to Facebook’s settings and choose Security and Login. About halfway down the page you’ll see an option for Two-Factor Authentication. One of the options will be Use two-factor authentication. Click the Edit button next to this option. You’ll see options for setting up either text-message based 2FA or an app like Google Authenticator. Open up the Google Authenticator app and either scan the QR code or type in the string of numbers that Facebook gives you. Facebook will now show up in your list of accounts in Google Authenticator.
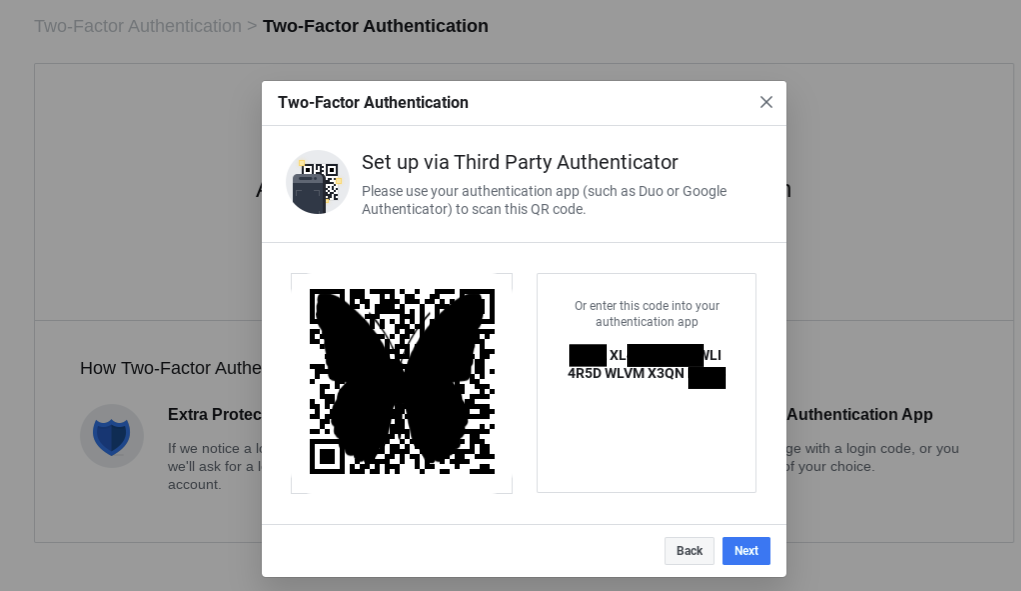
The next time you login to Facebook, you’ll enter your username and password as you usually do. Then you’ll be prompted to enter a second set of numbers from Google Authenticator as your two-factor security.
Open Google Authenticator and scroll down until you find the numbers generated for your Facebook account. Facebook will validate the numbers and allow you to access your account. The screenshot below shows the numbers generated. The circular shape to the right is counting down the time until another set of numbers is generated. (The black bars are covering the site names and login emails associated with each Google Authenticator number.)
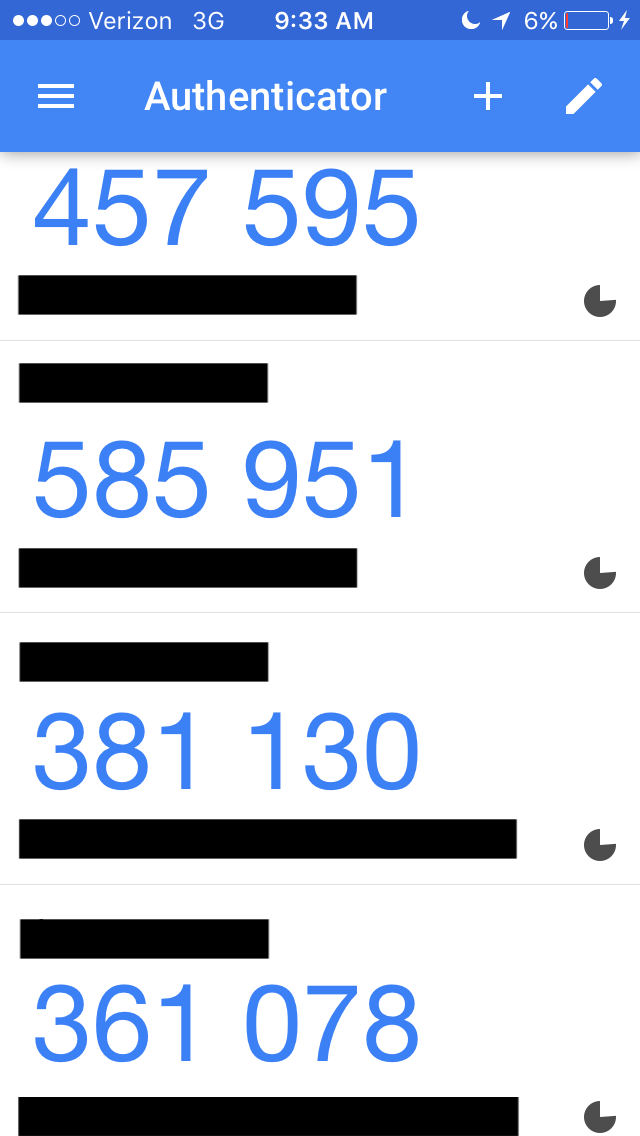
Google Authenticator used to be open source but is now proprietary. If you don’t want to use a Google product, there’s also Authy. Authy is not only available for mobile devices but also your desktop, too. In addition, you can set up Authy so that it syncs your 2FA security tokens across multiple devices. (I’m a little too paranoid for this, but I can see where it would come in handy if you’re sharing login information with family members or you use just a couple of devices to the exclusion of anything else).

Though they’re more secure than text messages, I do worry about apps. I don’t like having one more incredibly important thing on my phone. On a couple of occasions, my phone has run out its battery and I had to plug it in and wait for it to recharge before I could open the Google Authenticator app and log in to a website.
My Personal Favorite 2FA Method: A Hardware Token
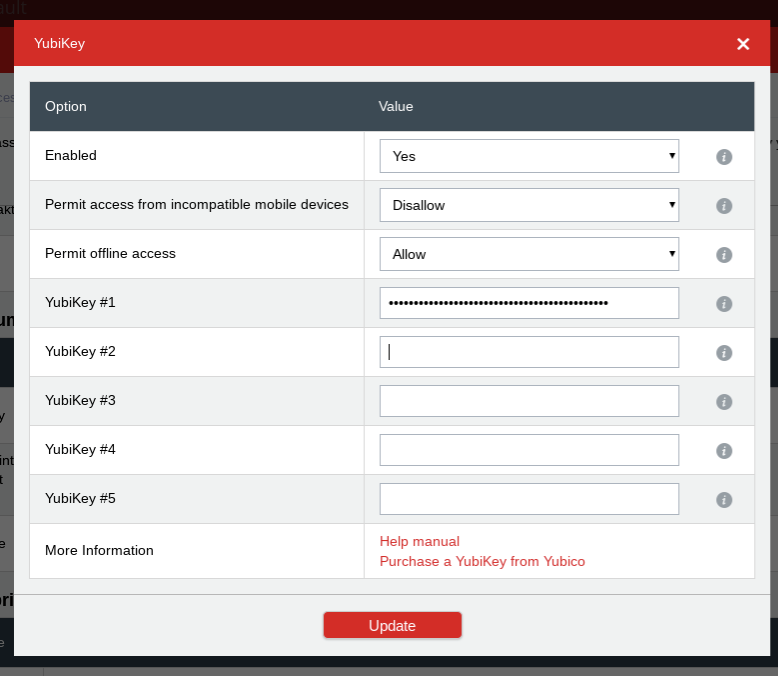
Because of these concerns I eventually moved away from the Google Authenticator app and settled on a security method I still use now: a hardware token. A hardware token (also called a security token) is a small device that you plug in to the computer as the second step in 2FA. I use one called a YubiKey.
When you first see a YubiKey, you might think it looks a bit like a flash drive.

See that gold circle with the y in the middle? That’s how the YubiKey works. Once I’ve entered my password on a site, I insert the YubiKey into a USB port and wait for that circle to light up. When it’s lit, I touch it, and it transmits a string of characters to the Web site and logs me in. (There is also a YubiKey product that can be used on mobile devices.)
I keep the YubiKey on my keychain, and my keychain on a lanyard that’s secured around a belt loop on my jeans and put in my front pocket. (It might look a little goofy, but I never lose my keys.) I always have it with me. It doesn’t have to be charged up. I don’t have to take it out and unlock it. It’s just right there.
Securing Your 2FA
You might be thinking “This sounds great, but you may still lose your keys at some point. What happens then? Are you locked out of your own accounts forever? Isn’t this 2FA business just too complicated?”
That’s a really good question. The answer in this case is to remember good computing practices — and this means backups!
Start with Backups. And I Mean Literally
I don’t have one YubiKey, I have two. One rides around on my keychain, the other one sits safely in my office. They both work as 2FA devices. If I do lose my keys or get mugged, I have an extra. Google has instructions on using Google Authenticator for multiple devices. And of course, Authy already has ways to sync across more than one device.
There are also backup codes, which are available for some sites like Google.
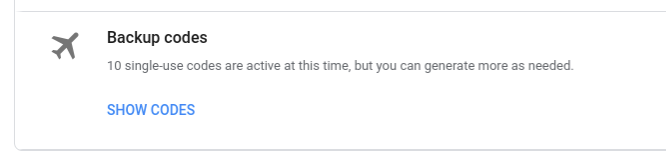
These codes allow you to log in to a site if you lose your 2FA device. Google gives you these codes ten at a time in a handy format that you can print out and stash in a safe place. Lifewire has a step-by-step article on how to generate and use these backup codes.
I wish I could say that if you implement these security measures, you will be absolutely protected against any kind of security problem on the Internet and you’ll never get hacked. I can’t say that because neither the Internet nor online security in general work that way. What I can say is that if you implement these security measures, you’ll be in a much better position to handle any security problems that come your way.
Featured image: Shutterstock.com
Become a Saturday Evening Post member and enjoy unlimited access. Subscribe now



Comments
Yes
I think a lot of people do not understand the importance of passwords and especially password managers. It’s a simple tool to use and improve your security online. Also, super convenient. Plenty of companies provide such services within various price ranges, like NordPass (https://nordpass.com/), LastPass (https://www.lastpass.com/) etc. What I like the most about password managers, that they usually warn you, if your password was compromised and generates complex passwords, so that you wouldn’t have to worry.